
Note: This article is biased on using proxies for social media accounts, and having the assumption that most of the users are using nefarious techniques while promoting, mostly resulting in spam activity and flagged IP’s and accounts. For other general usage purposes, almost any proxy provider can be good.
Very often I’m being asked what are my recommendation regarding proxies, questions that are in various forms ranging from “where do I get some good quality proxies” to “what proxies should I use to keep my accounts safe”. It looks like a usual question at first, only till you find out that there is no only black and white when it comes to proxies, due to some underlying factors unknown by the regular users, which I will try to list and explain below..
Shared proxies and their biggest (possible) drawback:
Shared proxies comes cheaper but they are usually shared between 3 users. While this can be a good compromise to keep costs down while having decent results, it may come down to what sites any of the 3 users are using the proxy for. A best case scenario is that neither of the users will use the same site others are using, but, especially in the CPA or PPI systems where thousands of marketers are promoting on about maximum top 10 most popular networks, and more than half of those are using a handful of the same proxy providers, the probability makes it very likely that at least two of the shared proxy owners to use it for the same site.
Implications of the fact above are having a fairly big impact on the ‘quality’ of the proxy itself, and that because once a social network is issuing a flag for an IP address, the sanctions that comes with it are affecting all the accounts logging through it. This will lead to quality complaints from some unfortunate users, and positive reviews from the luckiest ones. So what it will be ?.. A good or a bad proxy provider ? My opinion: just bad luck.
While some proxy providers ask their users for what sites are they going to use the proxies for, and then making sure to not assign the same proxies to another users using the same site, making a splitting to keep proxies safer – this doesn’t stop any user to use other site that he initially stated when ordering his shared proxy package, and as long as things are rapidly changing in CPA and PPI, many marketers are very likely to use the proxies for other sites that they initially wanted for, including one that can cross with yours, thus lowering your maximum allowed actions on the IP, which I will debate below..
IP limiting explained:
Think of IP limiting as road speed limits for cars, meaning one social network has set limits to only allows a maximum number of actions per day per IP (or per IP subnet). Similar to being ticketed on the road, when the limits are crossed on a social network, you get the IP flagged for suspicious activity. And this comes with various applied penalties including warnings, temporary blocks and bans.
More bad news: Because IP filtering can be applied for a whole IP subnet, this can also affect dedicated proxies from the same provider! User case: If three shared users are getting the IP 188.34.58.21, while performing unnatural/spam activity on the same site, it can also affect all the IP’s in the range 188.34.58.xx, or even 188.34.xx.xx. So a user of the dedicated IP 188.34.58.89 or 188.34.57.xx, who happens to use the same site, will receive a part of the damage that can put his social account at risk, because IP limits were crossed globally.
Manual blacklist applied to whole IP ranges and subnets known to be proxies:
This can be very easily done by staff in the anti-spam team of a social network, by monitoring popular Internet marketing forums and groups, and observing what proxy provides are mostly used for their site – they can compile lists of whole IP ranges from those providers. Next logical action is applying a lower trust factor, temporary blocks or simply completely blacklisting all these IP’s from using their site. With many marketers getting their accounts blocked or banned in a matter of hours or days, the result will obviously be a wave of quality complaints from all the clients of a particular proxy provider.
Such a filter update can’t be foreseen, and neither officially recognized, and the proxy provider can’t be put to blame.
The concept of ‘valid signals’ or something that can affect all types of proxies:
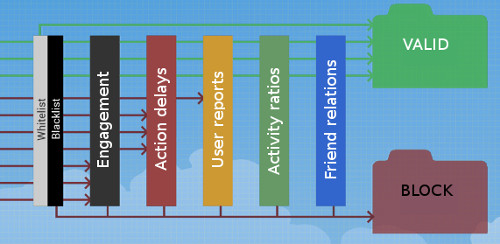
Valid signals is what is believed to be ordinary / authentic user actions on a social network platform. It is the recorded data of what is considered to be – real user activity, converted into complex mathematical graphs and formulas, that anti-spam algorithms can later compare with other new user data, and then pointing out any patterns that are out of the ordinary activity. It is a continuously-updated well crafted system, well guarded by their makers, where the keys to the enigma of blocked and banned accounts are laying.
The efficiency of these systems in detecting spam accounts is very high, thus resulting in lots of accounts being blocked, or completely banned.
While this is a completely new line of defense in the anti-spam filters of a social network, it has some ties with the IP’s being used for the accounts, because ultimately, new filters can be applied at the IP level (ranges and subnets) on the proxies the accounts were running on, affecting other proxy clients too.
Fingerprinting of TCP/IP stack and proxy software:
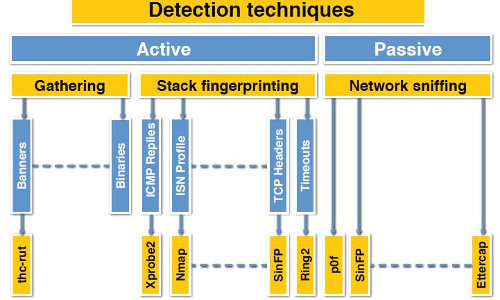
Detecting various particularities at the hardware and software levels used for the deployment of the proxy can lead to automated blacklist. A proxy can be deployed in many ways and can have hundreds of unique characteristics, and in a few specific situations, it comes with weak points that can make it easily marked as a proxy by social networks. And these settings and environmental variables of the proxy can only be modified by the server administrator, leaving regular proxy clients without altering options. I will list below the most common traces a proxy can leave behind:
- TCP timestamp: It can determine system uptime value of the proxy server.
- TCP options and their order: Identifies unique characteristics of the TCP features on the proxy server.
- HTTP responses and header order: HTTP responses and header order can slightly vary from server to server, this leads to fingerprinting of the machine.
- HTTP response to malformed TCP packets: Different servers respond in various ways to malformed HTTP requests, making it for one more way of fingerprinting.
There are many more methods of fingerprinting at the TCP/IP and HTTP protocol levels, but for the purpose of this article I believe there are enough examples, and obfuscating the traces above makes it for the subject of another article.
CONCLUSION:
When trying to find a good proxy provider for social media accounts, the best advice I can give is to avoid mainstream providers that everybody seems to use. Ideally the provider should not be very popular among IM forums, and not listed among the first choices for CPA marketers. The reason: it will be saturated by too many CPA marketers (this monetization consists of mostly questionable offers that get quickly marked as spam), thus adding the provider on the flagged/blacklisted IP’s list in a given social network.
However, if you want to see some proxy recommendations, here is a list of the best proxy providers on the market.
The cheapest proxies on the market are usually used by the most people, and when they’re used on big sites with high anti-spam filters like Facebook or Instagram for example, these will be the most flagged proxies that you can get. So instead of going with the cheapest, and especially the ones that are having the same IP with different port (11.11.11.11:10001; 11.11.11.11:10002), you’ll be way better with even medium priced proxies like the semi-dedicated ones (shared) for about $1/proxy.


